Authentication vs Authorization
This article distinguishes between authentication and authorization, two fundamental concepts in security. Understanding their differences is essential for system design interviews and building secure applications.
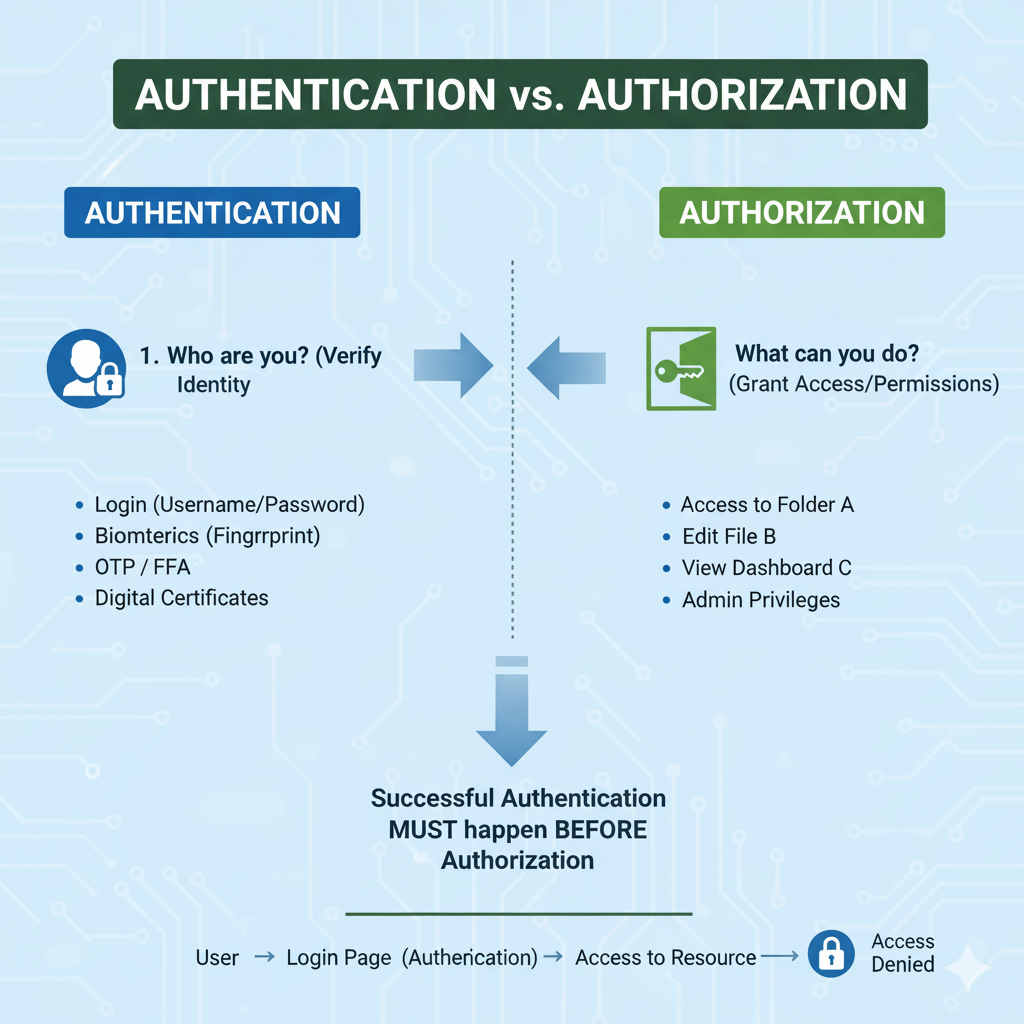
What is Authentication?
Authentication (often abbreviated as "authn") is the process of verifying the identity of a user, device, or system. It answers the question: "Who are you?"
How Authentication Works
Authentication typically involves:
- Credentials Submission: The user provides proof of identity, such as a username/password, token, or biometric data.
- Verification: The system checks these credentials against stored data (e.g., a hashed password in a database).
- Session Creation: Upon success, a session or token is issued to maintain the authenticated state.
Common Authentication Methods
- Username/Password: Basic but vulnerable to breaches; use hashing (e.g., bcrypt) and salting.
- Multi-Factor Authentication (MFA): Combines something you know (password), have (token/app), or are (biometrics).
- OAuth 2.0/OpenID Connect: Delegated authentication for third-party apps (e.g., "Sign in with Google").
- JWT (JSON Web Tokens): Stateless tokens for API authentication.
- Certificate-Based: Uses digital certificates for machine-to-machine auth (e.g., TLS client certificates).
Challenges: Phishing, credential stuffing, and weak passwords. Best practices include rate limiting, CAPTCHA, and password policies.
What is Authorization?
Authorization (often abbreviated as "authz") is the process of determining what an authenticated user is allowed to do. It answers the question: "What can you do?"
How Authorization Works
Authorization occurs after authentication and involves:
- Policy Evaluation: Checking user roles, permissions, or attributes against access control rules.
- Resource Access: Granting or denying access to specific resources (e.g., files, APIs, databases).
- Enforcement: The system blocks unauthorized actions, often logging them for auditing.
Common Authorization Models
- Role-Based Access Control (RBAC): Users are assigned roles (e.g., admin, user), and roles have permissions (e.g., read/write).
- Attribute-Based Access Control (ABAC): Decisions based on attributes (e.g., user location, time of day, device type).
- Access Control Lists (ACLs): Explicit lists of users/groups allowed/denied for a resource.
- OAuth Scopes: In API contexts, scopes define granular permissions (e.g., read:email, write:posts).
Challenges: Over-privileging (principle of least privilege), policy complexity, and dynamic changes in user roles.
Key Differences: Authentication vs Authorization
| Aspect | Authentication | Authorization |
|---|---|---|
| Purpose | Verify identity ("Who are you?") | Grant permissions ("What can you do?") |
| Timing | First step in access flow | After successful authentication |
| Outcome | User/session is validated | Access to resources is allowed/denied |
| Examples | Logging in with password | Admin can delete users; user can read |
| Failure | Access denied (401 Unauthorized) | Access denied (403 Forbidden) |
| HTTP Status | 401 (Unauthenticated) | 403 (Unauthorized in some contexts) |
Note: In HTTP, 401 is for unauthenticated (retry with credentials), while 403 is for authenticated but unauthorized.
Analogy
Authentication is like showing your ID at a club entrance. Authorization is like the bouncer checking if your ID allows VIP access or just the dance floor.
Real-World Integration
In modern systems:
- AuthN + AuthZ Flow: A user authenticates via OAuth, receives a token, and the token's claims (e.g., roles) are used for authorization.
- Tools/Frameworks: Use libraries like Spring Security (Java), Passport.js (Node.js), or Auth0 for handling both.
- Zero Trust Model: Assumes no implicit trust; re-authenticate and re-authorize continuously.
Common Pitfalls
- Confusing the two: Implementing authz without proper authn exposes systems.
- Token Management: Secure storage (e.g., HttpOnly cookies for JWTs) and short expiration times.
- Scalability: Centralized auth (e.g., LDAP) vs. federated (e.g., SAML).
Real-World Context
- Interview Relevance: System design questions often involve secure access patterns (e.g., "Design a microservices auth system"). Explain how authn feeds into authz.
- Practical Use: In cloud environments (AWS IAM, Azure AD), authn verifies identity, while policies enforce authz. Critical for compliance (GDPR, HIPAA).
- Modern Trends: Passwordless auth (e.g., WebAuthn), AI-driven anomaly detection, and blockchain for decentralized identity.
Further Reading
- Security Engineering by Ross Anderson
- OAuth 2.0 RFC (RFC 6749) and OpenID Connect specs
- OWASP Authentication Cheat Sheet
- Blogs from Auth0, Okta, and NIST on best practices