Public Key Cryptography (RSA, SSL/TLS)
Public key cryptography, also called asymmetric cryptography, is the backbone of secure communication on the internet.
It powers HTTPS, digital signatures, and modern authentication systems.
This article explores RSA, how it works, its role in SSL/TLS, and modern perspectives.
1. Why Public Key Cryptography?
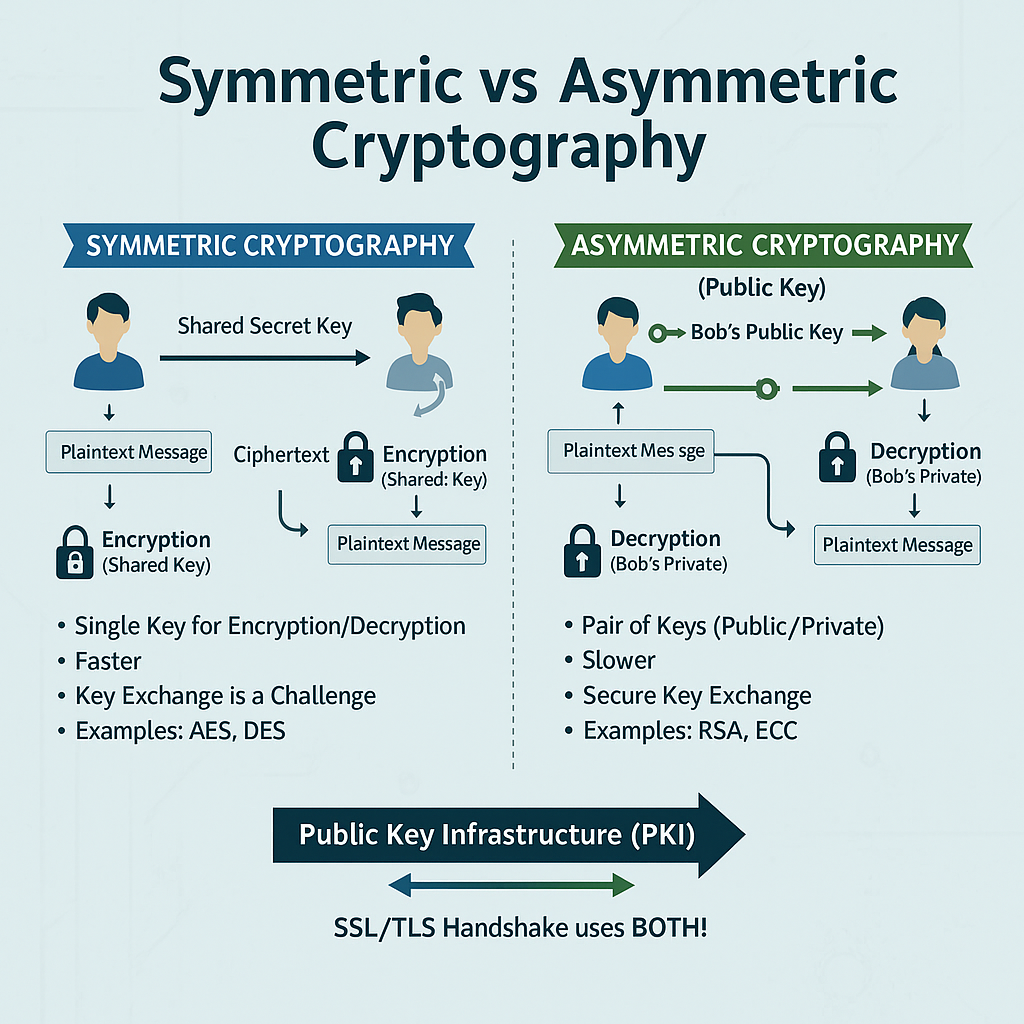
Before public key cryptography, systems relied on symmetric encryption (same key for encryption & decryption).
Problem → Key Distribution: How do you securely share the secret key over an insecure network?
Asymmetric cryptography solves this:
- Each user has a public key (shareable) and a private key (kept secret).
- Data encrypted with one can only be decrypted with the other.
✅ This enables secure communication without pre-sharing a secret key.
2. RSA: The Foundation
RSA (Rivest–Shamir–Adleman, 1977) is one of the earliest and most widely used asymmetric algorithms.
Its security relies on the difficulty of factoring very large integers.
2.1 How RSA Works
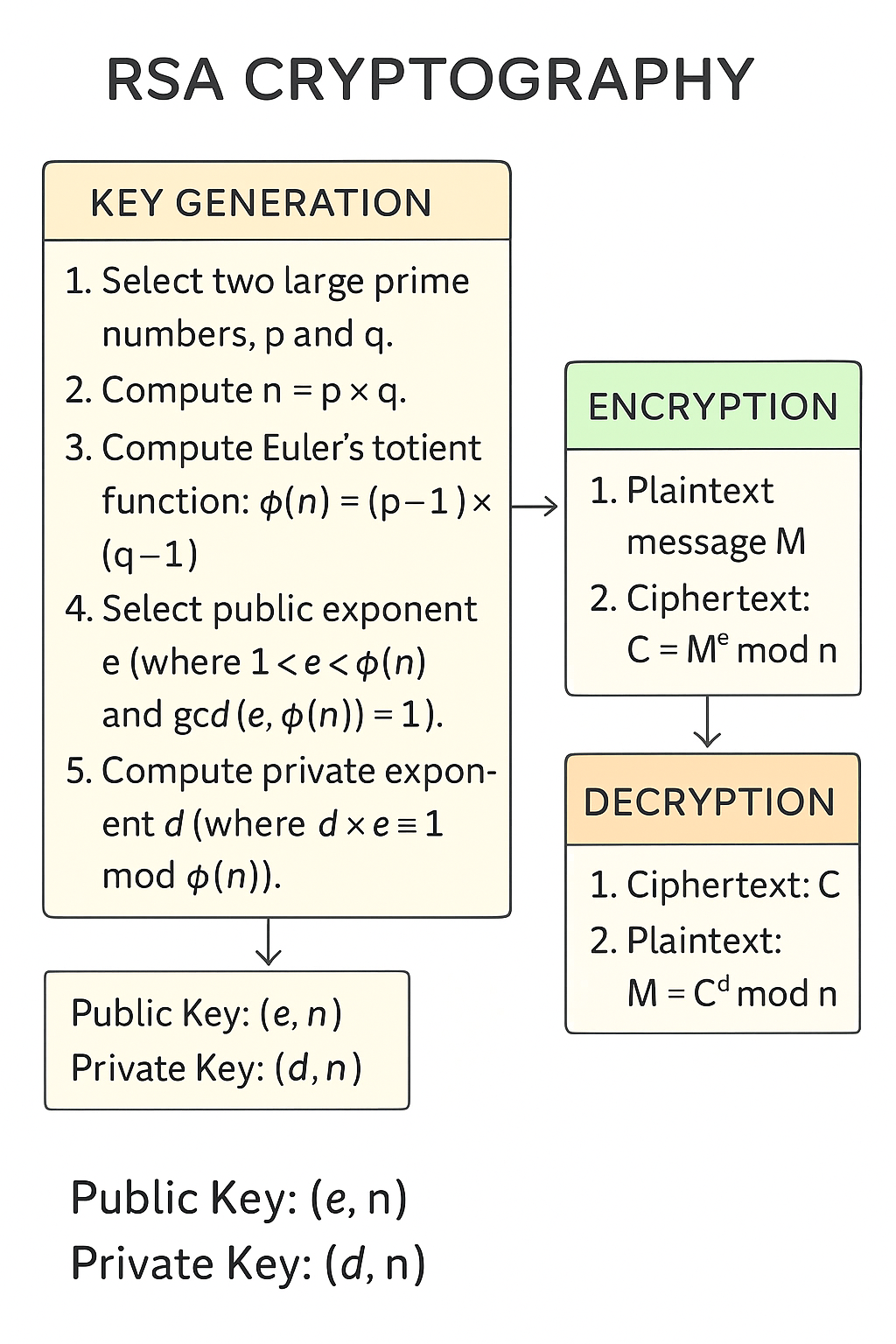
Key Generation
- Choose two large primes and .
- Compute .
- Compute .
- Choose a public exponent (commonly ) such that .
- Compute the private exponent such that .
- Public key: ; Private key: .
Encryption
- Sender computes .
- is the ciphertext sent to the recipient.
Decryption
- Recipient computes .
Digital Signatures
- Sender hashes the message to produce and computes the signature .
- Recipient verifies by computing and checking .
2.2 Example (Small Numbers)
Note: toy example for illustration only (not secure).
- Let and , so .
- Then .
- Choose (which is coprime with 3120).
- Compute (the modular inverse of 17 modulo 3120).
- Public key: ; Private key: .
Encrypt message :
- .
Decrypt:
- .
3. Limitations of RSA
- Performance → RSA is computationally expensive for large data.
- Padding Requirements → Raw RSA is insecure; use padding schemes such as OAEP for encryption and PSS for signatures.
- Lack of Forward Secrecy → If a server's long-term private key is compromised, past sessions using RSA key exchange can be decrypted.
- Key Size → Secure RSA generally requires 2048–4096 bit keys (larger than comparable ECC keys).
📌 Why not use RSA for everything? → RSA is typically used to securely exchange a symmetric session key (e.g., for AES), and symmetric ciphers are used for bulk data encryption.
4. Public Key Cryptography in SSL/TLS
Public key cryptography is fundamental to HTTPS (SSL/TLS), which secures web communication.
4.1 TLS Handshake (Simplified)
- Client Hello → Browser sends supported ciphers and a random nonce.
- Server Hello → Server responds with chosen cipher suite and its certificate (containing the server's public key).
- Key Exchange →
- Older TLS used RSA to encrypt a session key.
- Modern TLS (1.3) prefers ephemeral Diffie–Hellman (usually ECDHE) for forward secrecy.
- Session Key Established → Both parties derive the same symmetric session key from exchanged material.
- Secure Communication → Application data is encrypted with a symmetric cipher (e.g., AES-GCM or ChaCha20-Poly1305).
4.2 Certificates & Certificate Authorities (CAs)
- Servers prove identity using X.509 certificates signed by trusted Certificate Authorities (CAs).
- Browsers and OSes maintain root CA trust stores; a certificate chain is validated up to a trusted root.
📌 Interview Tip: Explain why TLS combines asymmetric cryptography (for auth/key exchange) with symmetric cryptography (for performance).
5. Modern Cryptography Beyond RSA
- Elliptic Curve Cryptography (ECC) → Provides similar security with much smaller key sizes (e.g., a 256-bit EC key ≈ 3072-bit RSA). Algorithms: ECDSA (signatures), ECDHE (ephemeral key exchange).
- TLS 1.3 → Emphasizes ephemeral Diffie–Hellman (ECDHE) for forward secrecy and removes many older insecure options.
- Post-Quantum Cryptography (PQC) → Quantum algorithms (e.g., Shor's algorithm) could break RSA/ECC. NIST is standardizing PQC algorithms (e.g., CRYSTALS-Kyber for KEMs).
6. Real-World Context & Interview Tips
Interview Relevance
- Know RSA key generation and why RSA is used for key exchange (and not for bulk encryption).
- Be able to describe a TLS handshake at a high level and explain forward secrecy.
Practical Use
- RSA/ECC are used for HTTPS, SSH, software signing, and secure messaging.
Analogy
- RSA is like a locked mailbox: the public key is the slot (anyone can drop a message in), while the private key is the physical key to open the mailbox.
7. Further Reading
- Cryptography and Network Security — William Stallings
- Applied Cryptography — Bruce Schneier
- RFC 8446 (TLS 1.3 Specification)
- NIST Post-Quantum Cryptography Project