Hashing vs Encryption
Hashing and encryption are two fundamental concepts in security that are often confused.
Both transform data, but they serve very different purposes:
- Hashing ensures integrity (data has not been tampered with).
- Encryption ensures confidentiality (data is hidden from unauthorized users).
Understanding the distinction is critical in system design interviews and for building secure applications.
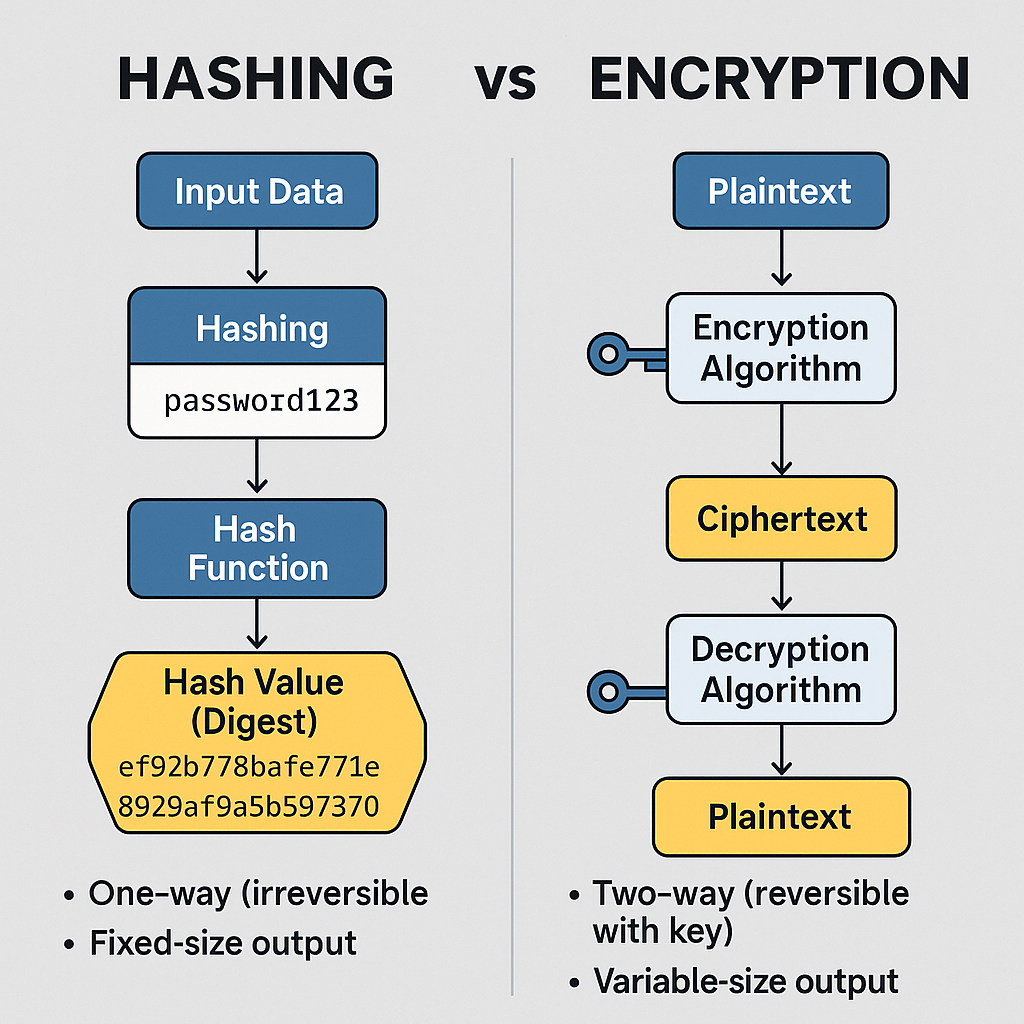
1. What is Hashing?
Hashing is a one-way process that transforms input data (of any size) into a fixed-size output, called a hash value or digest.
It is irreversible, meaning you cannot reconstruct the original input from the hash.
Key Characteristics
- Deterministic: Same input → same output.
- Fixed Output Size: Input can be 1 byte or 1 GB, output length is constant (e.g., 256 bits for SHA-256).
- Collision Resistance: Hard to find two inputs that produce the same hash.
- Preimage Resistance: Given a hash, infeasible to reverse it to the input.
- Avalanche Effect: Small input changes drastically change the output.
- Fast Computation: Efficient for large-scale use.
Common Algorithms
- MD5 → Obsolete (broken).
- SHA-1 → Deprecated.
- SHA-256/SHA-3 → Secure, widely used.
- bcrypt / scrypt / Argon2 → Designed for password hashing (slow + salted).
Use Cases
- Password Storage: Store salted & hashed passwords instead of plaintext.
- Integrity Checks: File checksums (e.g., software downloads).
- Digital Signatures: Hash message before signing.
- Blockchain: Links blocks securely using hash chains.
Best Practice: For password hashing, always use salt + slow functions (bcrypt, Argon2). Consider adding a "pepper" (a secret key stored separately).
2. What is Encryption?
Encryption is a reversible process that transforms plaintext into ciphertext using a key.
Decryption recovers the original data with the correct key.
Key Characteristics
- Reversible: Requires correct key for decryption.
- Key Dependency: Security depends on the secrecy of the key.
- Confidentiality: Protects data from unauthorized access.
- Variable Output Size: Ciphertext size grows with input.
Types of Encryption
Symmetric Encryption
- Same key for encryption & decryption.
- Example: AES-256 (fast, secure).
- Challenge: Secure key distribution.
Asymmetric Encryption
- Public key for encryption, private key for decryption.
- Example: RSA, ECC.
- Slower, used for key exchange, digital signatures.
Use Cases
- Secure Communication: HTTPS/TLS.
- Data Protection: Disk encryption, encrypted databases.
- Key Exchange: Asymmetric used to share symmetric keys.
- Digital Signatures: Encrypt hash with private key to prove authenticity.
3. Key Differences: Hashing vs Encryption
| Aspect | Hashing | Encryption |
|---|---|---|
| Purpose | Integrity, verification | Confidentiality, secrecy |
| Reversibility | One-way (irreversible) | Two-way (reversible with key) |
| Output | Fixed-size digest | Variable-size ciphertext |
| Key Usage | No key (uses salt/pepper for passwords) | Requires key(s) |
| Examples | SHA-256, bcrypt | AES, RSA |
| Use Case | Password storage, checksums | Secure communication, data protection |
| Performance | Very fast | Slower (especially asymmetric) |
| Analogy | Fingerprint: unique, can’t reconstruct | Locked box: key opens to original data |
4. When Hashing and Encryption Work Together
Many secure systems combine both:
- Digital Signatures → Message is hashed, then hash is encrypted with private key.
- TLS/HTTPS → Uses asymmetric encryption to exchange keys, then symmetric encryption for data, plus hashing for integrity.
This layered approach ensures confidentiality, integrity, and authenticity.
5. Practical Considerations
Hashing
- Always salt passwords before hashing.
- Use slow, memory-hard algorithms (Argon2, bcrypt).
- Never use MD5 or SHA-1 for security.
Encryption
- Use AES-256 for data-at-rest or in-transit.
- Use RSA/ECC only for key exchange, not bulk data.
- Protect encryption keys (e.g., with HSMs or KMS).
Common Mistakes
- Encrypting passwords instead of hashing them.
- Using weak hash functions in security-critical systems.
- Confusing integrity (hash) with confidentiality (encryption).
6. Real-World Context
- Interview Relevance: Expect questions like “How would you store user passwords securely?” or “Why not encrypt passwords instead of hashing?”
- Practical Use: Hashing → blockchain, password security; Encryption → HTTPS, VPNs, cloud storage.
- Modern Trends:
- Post-quantum encryption to resist quantum attacks.
- GPU-resistant hashing (e.g., Argon2) to prevent brute-force.
7. Further Reading
- Cryptography and Network Security — William Stallings
- OWASP Password Storage Cheat Sheet
- NIST SP 800-63B (Digital Identity Guidelines)
- Cloudflare, Okta, AWS blogs on security practices